Expert Hub
Effortless Control: A Guide to User Management with Keap
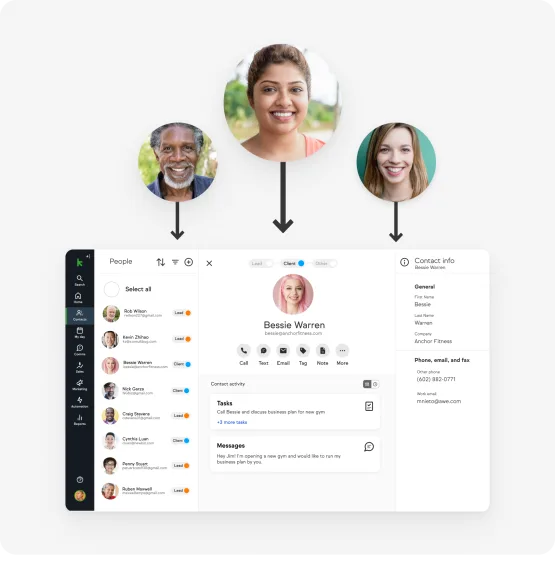
User Roles and Permissions
- Admin vs. User Roles: Differentiate between admin and user roles and their respective permissions.
- Custom Roles: Create custom roles to precisely match your organization’s structure.
- Access Control: Manage access to specific features and functionalities based on roles.
Ensuring Secure Access: User Authentication and Permissions
Security is paramount in user management. Dive into Keap’s features that enhance user authentication and implement measures to safeguard sensitive information.
- Two-Factor Authentication: Enable two-factor authentication for an additional layer of security.
- IP Restriction: Implement IP restrictions to control access from specific locations.
- Audit Trails: Monitor and review user activities through Keap’s audit trail features.
Managing users includes understanding when to deactivate accounts and how to handle data associated with deactivated users. This section provides guidance on efficient user deactivation and data management.
- Deactivation Protocols: Establish protocols for deactivating user accounts when needed.
- Data Ownership: Define data ownership policies and procedures for seamless transitions.
- Archiving User Data: Safely archive data associated with deactivated users for compliance.

Collaboration Excellence: Utilizing Keap's Communication Features
Keap offers communication tools to enhance collaboration. Explore how to leverage these features to facilitate seamless communication among users.
- Internal Messaging: Use Keap’s internal messaging for quick and secure team communication.
- Task Assignment: Assign tasks within Keap to streamline collaborative projects.
- Shared Calendars: Utilize shared calendars to coordinate schedules and deadlines.


